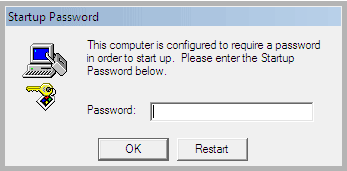
Some RansomWare Viruses and "Microsoft Tech" Scammers will Enable Windows' "SysKey" Function,
and lock you out of your computer!
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
*THIS IS FOR WINDOWS 7; MAY WORK ON 8 or 10 BUT THIS IS NOT TESTED OR CONFIRMED.
If this happens to you, the first thing you can try is use a Windows OS Media disk to remove the "SysKey" function using the Command Line.
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
- Boot to the appropriate OS Media (matches the installed OS version of the computer you are fixing).
- When the OS installation screen comes up, Select USA English and then "Repair the Windows Installation"; DO NOT INSTALL!!
- Go to "Advanced Troubleshooting"
- Click on "Advanced Repairs"
- Click on and open the the "Command Line" tool
- Find the OS Disk by changing drive letters and checkin contents with the "dir" command. ie: cd C: cd D: cd E:, etc.
- Run the following command on the OS drive:
copy c:\windows\system32\config\regback c:\windows\system32\config - Say no to the "Software" replace prompt, but say yes to the others and replace a total of 4 files; Default, SAM, Security and System.
- Reboot system
A warning however, you may have some security, OS and/or user account damage after the fact.
However there is an alternate method (or two) that can also do the trick, if the above process does not work, or is too difficult!
I have also removed the "Syskey" password using the following procedure:- Boot from a Windows 7 Install DVD/Thumbdrive, or boot from a user created Windows Restore/Repair Thumb Drive.
*You can also attempt the same procedure from Windows Start-Up Repair; if you are able to get there. - When the "Install Windows" screen appears, click on "Repair your computer" to access the system recovery options.
- From the nex screen, run System Restore to last point before the syskey password on your computer.
*This will fail, but must be done! - Click "run system restore again" and this will take you back to the main system recovery options list.
- Open Command Prompt from the main system recovery options list.
- Open Regedit; type "regedit" without the quotes, into the command prompt and the Regedit application will open.
- Navigate to: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa and change the 'SecureBoot' value entry from 1 to 0.
- Navigate to: HKEY_LOCAL_MACHINE \SAM\SAM\Domains\Account and delete everything for "F value" so that it's data/value is 0000
- Reboot and you should now be able to Login!
If you are not able to boot into the Windows 8 or 10 Startup Recovery Environment there is still yet another repair method you can try!
To get the computer to run a system restore if you can't get into the recovery environment, you try to make/trip the computer into doing a Startup Repair.- The way we do this, is by turning the system off mid boot and then Startup Repair should catch that "issue" and run the next time you power on.
- During this process Windows typically recommends running a system restore to fix any possible boot issues; allow this process to proceed and complete.
- After this process has completed, open the computer's DVD drive and insert a copy of Hiren's All-in-one Boot CD/thumb drive.
- Turn the system off/restart the system.
- Booting from DVD or USB, boot into the Hiren's All-in-one Media and select "Mini XP Recovery Environment"
- Allow your system to boot into the "Mini XP Recovery Environment" RAM Drive environment.
- Once booted into "Mini XP" you can now run the built in Registry Editor (regedit) to complete the registry edits needed and listed in the previous repair steps.
These all have worked for me on client machines and has allowed me to get passed a "syskey" password each time. Once I am able to login to the client's system, I will physically disconnect the internet and start my cleaning procedures on the affected system. After a full clean-up, software removal and tune-up the once locked PC will now run fine without the user getting locked out anymore!
I hope this helps general users or other IT professionals!
Pacific Northwest Computers
Jon Pienkowski - Owner/Operator
www.pnwcomputers.com
360.624.7379








