With more than 20 years of experience, Pacific NorthWest Computers provides affordable on-site and in-shop computer repair services in Washington and Oregon State! We provide services ranging from onsite and remote support, malware removal, data recovery, laptop hardware repairs, custom-built computers, networking, security services, consulting/training, and many other computer/tech-related support and services! www.linktr.ee/pnwcomputers
Showing posts with label hackers. Show all posts
Showing posts with label hackers. Show all posts
Monday, October 14, 2024
Monday, January 21, 2019
RansomWare or a Fake Tech Scammer Locked You Out of Your Computer using a "SysKey" Password
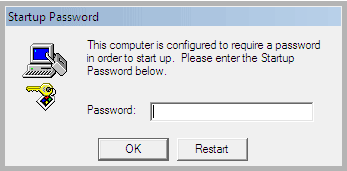
Some RansomWare Viruses and "Microsoft Tech" Scammers will Enable Windows' "SysKey" Function,
and lock you out of your computer!
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
*THIS IS FOR WINDOWS 7; MAY WORK ON 8 or 10 BUT THIS IS NOT TESTED OR CONFIRMED.
If this happens to you, the first thing you can try is use a Windows OS Media disk to remove the "SysKey" function using the Command Line.
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
- Boot to the appropriate OS Media (matches the installed OS version of the computer you are fixing).
- When the OS installation screen comes up, Select USA English and then "Repair the Windows Installation"; DO NOT INSTALL!!
- Go to "Advanced Troubleshooting"
- Click on "Advanced Repairs"
- Click on and open the the "Command Line" tool
- Find the OS Disk by changing drive letters and checkin contents with the "dir" command. ie: cd C: cd D: cd E:, etc.
- Run the following command on the OS drive:
copy c:\windows\system32\config\regback c:\windows\system32\config - Say no to the "Software" replace prompt, but say yes to the others and replace a total of 4 files; Default, SAM, Security and System.
- Reboot system
A warning however, you may have some security, OS and/or user account damage after the fact.
However there is an alternate method (or two) that can also do the trick, if the above process does not work, or is too difficult!
I have also removed the "Syskey" password using the following procedure:- Boot from a Windows 7 Install DVD/Thumbdrive, or boot from a user created Windows Restore/Repair Thumb Drive.
*You can also attempt the same procedure from Windows Start-Up Repair; if you are able to get there. - When the "Install Windows" screen appears, click on "Repair your computer" to access the system recovery options.
- From the nex screen, run System Restore to last point before the syskey password on your computer.
*This will fail, but must be done! - Click "run system restore again" and this will take you back to the main system recovery options list.
- Open Command Prompt from the main system recovery options list.
- Open Regedit; type "regedit" without the quotes, into the command prompt and the Regedit application will open.
- Navigate to: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa and change the 'SecureBoot' value entry from 1 to 0.
- Navigate to: HKEY_LOCAL_MACHINE \SAM\SAM\Domains\Account and delete everything for "F value" so that it's data/value is 0000
- Reboot and you should now be able to Login!
If you are not able to boot into the Windows 8 or 10 Startup Recovery Environment there is still yet another repair method you can try!
To get the computer to run a system restore if you can't get into the recovery environment, you try to make/trip the computer into doing a Startup Repair.- The way we do this, is by turning the system off mid boot and then Startup Repair should catch that "issue" and run the next time you power on.
- During this process Windows typically recommends running a system restore to fix any possible boot issues; allow this process to proceed and complete.
- After this process has completed, open the computer's DVD drive and insert a copy of Hiren's All-in-one Boot CD/thumb drive.
- Turn the system off/restart the system.
- Booting from DVD or USB, boot into the Hiren's All-in-one Media and select "Mini XP Recovery Environment"
- Allow your system to boot into the "Mini XP Recovery Environment" RAM Drive environment.
- Once booted into "Mini XP" you can now run the built in Registry Editor (regedit) to complete the registry edits needed and listed in the previous repair steps.
These all have worked for me on client machines and has allowed me to get passed a "syskey" password each time. Once I am able to login to the client's system, I will physically disconnect the internet and start my cleaning procedures on the affected system. After a full clean-up, software removal and tune-up the once locked PC will now run fine without the user getting locked out anymore!
I hope this helps general users or other IT professionals!
Pacific Northwest Computers
Jon Pienkowski - Owner/Operator
www.pnwcomputers.com
360.624.7379
Labels:
computer,
extortion,
fake tech support,
hack,
hackers,
locked out,
online scam,
password,
pc,
ransomware,
scam,
scammers,
syskey,
tech scam,
Virus
Friday, June 5, 2015
How can I keep my computer from getting infected? Pacific NW Computers' PC Security Tips
1. Make sure you
regularly run MANUAL scans with your installed security software!
Security Programs We
Recommend (Or Have Installed):
- Avast Antivirus, BitDefender Free, Microsoft Security Essentials
- MalwareBytes Anti-Malware
- Spybot Search & Destroy
- CCleaner
http://pnwcomputers.blogspot.com/2013/06/pnw-computers-links-and-recommended.html
Basic/General Scanning
Procedure:
- Before running
any scans with any of the installed security software, be sure to FULLY
update the software FIRST.
- After updating
the security software, perform the deepest and most thorough scan that the
software is capable of. This is usually labeled as a FULL or COMPLETE scan.
- DELETE or
QUARANTINE any and all of the security software’s findings.
- Make sure you
DON’T download and install any scanner/security software that solicits you
to download and install its software. These scanners are blacklisted
because of their questionable reputation.
2. Make sure your
Windows is ALWAYS up to date!
- An unpatched
Windows is vulnerable and even with the “best” Antivirus installed;
malware will find its way through.
So visit http://windowsupdate.microsoft.com/ to download and install the latest updates. - Be sure to download and install all CRITICAL and SOFTWARE updates! You also may have to do several “passes” of Windows updates before all the available updates/patches are actually installed.
- Verify that your
version of Windows Vista, Windows 7 or Windows 8 has the most recent service pack installed. If this is not currently installed on your system, the Windows Update
website will recognize this vulnerability and request you to download and
install any available Service Packs and other needed updats.
3. Stay away from
questionable sites.
- This is one of
the main causes why a computer gets infected. Visiting
cracksites/warezsites – and other questionable/illegal sites is ALWAYS a
risk. Even a single click on the site can be responsible for installing a
huge amount of malware. Don’t think: “I have a good Antivirus and Firewall
installed, they will protect me” – because that’s not true… there is no
“Magic Bullet”. Before you know it, your Antivirus and Firewall may
already be disabled because malware already found its way on your system.
4. Be careful with
email attachments!
- Malware spreads
via email as well, especially email attachments. The most common ones are emails
telling you that your computer is infected and that you can find the
removal tool in the attachment, emails telling you that your password has
changed and can find it in the attachment, emails with product codes in
the attachment from software that you purchased (which you didn’t), emails
with attachments that are so called “Security Updates”, etc. etc.
- Don’t trust any
emails like the ones listed above. Don’t even attempt to preview/open them
and delete them immediately instead! It may also happen you receive an
email from someone you know, but with a questionable attachment present
and strange content in the e-mail’s message. In this case, this person –
or someone else who has your address book in his/her address book – is
infected with malware (worm/spambot) and sends these emails without being
aware of it.
- Don’t click
links in emails from someone you don’t know, because these links can
redirect you to sites where malware gets downloaded and installed.
5. When surfing the
internet…
- Use Google Chrome or the FireFox
web browser as your MAIN internet browser. These browsers does not use
ActiveX controllers or BHO’s (these are programs that are a standard
feature’s of Microsoft’s Internet Explorer and are “exploited”
vulnerabilities that hackers use to infect computers). If a specific
website (such as a financial institution website) may require Internet
Explorer to be used in order for you to view their site, then use Internet
Explorer. But for that specific website ONLY!
- Don’t click on
links inside pop-ups. ALWAYS close the windows via the "X" for the window vs. clicking "Cancel" or any other 'escapes' in the pop-up.
- Download
software off of the internet from websites you know and trust. A lot of
free software comes bundled with other software, including malware.
- Be careful when
you are viewing videos online. Especially when you get a pop-up asking you
to download a “Codec” to be able to watch the video. By default, your
media player should already have the necessary codec installed to watch
online videos. In the case that you’re prompted to install an additional
codec while trying to watch a move online (or downloaded), it is most
likely a false alert and this so-called codec may install malware.
- Don’t install
plug-ins (ActiveX) if you’re not certain what it is or why it is you need
it. (Unless you are attempting to perform Windows/Microsoft Updates).
- Glubble is a
great FireFox add-on if you want to manage the sites your kids are allowed
to see.
6. Watch what you
download!
- If you want to
install certain software, always go to the developer’s site to download the
software. Then you can be sure you’re downloading and installing the right
software. Be aware of the fact that certain software (especially freeware)
may contain/come bundled with extra software including spyware and/or
adware. So only install when you’re sure they are OK.
- The use of Torrent sites, Game Patches and Mods, Emulators; really anything "Free" is always a risk. Unless the download/host site is a reputable site, you can never be sure what you are exactly downloading. A file you are looking to download or have downloaded isn’t always what it’s made out to be.
If you have any questions or comments please don't hesitate to get in touch!
Jon Pienkowski
Pacific NorthWest Computers
www.pnwcomputers.com
360-624-7379
Jon Pienkowski
Pacific NorthWest Computers
www.pnwcomputers.com
360-624-7379
Wednesday, April 30, 2014
Microsoft Internet Explorer Vulnerability ~ Fact and Opinion
As you have most likely heard, Microsoft is scrambling to fix a major bug which allows hackers to exploit flaws in Internet Explorer 6, 7, 8, 9, 10 and 11. The company has also confirmed it will not issue a fix for web browsers running on Windows XP after it formally ended support for the 13 year old operating system back on April 8th.
The vulnerability was discovered by cyber security software maker FireEye Inc. which stated the flaw is a ‘zero-day’ threat. This means the first attacks were made on the vulnerability before Microsoft was aware of it. FireEye also revealed a sophisticated hacker group has already been exploiting the flaw in a campaign dubbed ‘Operation Clandestine Fox’, which targets US military and financial institutions.
FireEye spokesman Vitor De Souza declined to name the hackers or potential victims as the investigation is ongoing, only telling Reuters: “It’s unclear what the motives of this attack group are at this point. It appears to be broad-spectrum intel gathering.”
For its part Microsoft has confirmed the existence of the flaw in an official post: https://technet.microsoft.com/library/security/2963983
Now, Internet Explorer has always been a vulnerable browser and has exploits created/identified against it everyday. This is why for YEARS I have pushed my customers to use an alternative Web Browser such as Mozilla Firefox or Google Chrome. As previously mentioned, both of those web browsers are safer to use than Internet Explorer and are both immune from the recently identified exploit!
What makes this recent vulnerability stand out from the others, and why this particular vulnerability is making all the headlines, is that the problem is pretty widespread; affecting 1 in 4 Windows based computers and ALL Windows XP systems.
A Temporary Fix
While Microsoft rushes to fix the bug, FireEye gave concerned users two workarounds .
- Use another web browser other than Internet Explorer
- Disable Adobe Flash. “The attack will not work without Adobe Flash,” it said. “Disabling the Flash plugin within IE will prevent the exploit from functioning.”
No Hope For Windows XP
Microsoft has confirmed that no fix will be rolled out for Windows XP because support has officially ended and there are no plans to make an exception. It states:
“An unsupported version of Windows will no longer receive software updates from Windows Update. These include security updates that can help protect your PC from harmful viruses, spyware, and other malicious software, which can steal your personal information.”
The company’s advice to Windows XP users has remained the same for some time: upgrade to Windows 7 or 8 or buy a new PC. It has also repeatedly sent a pop-up dialog box to reachable Windows XP machines with the following end of support notification.
For users unsure whether their existing XP PCs can support Windows 8, Microsoft offers a software tool called ‘Windows Upgrade Assistant’ which can be downloaded here: http://go.microsoft.com/fwlink/p/?LinkId=321548
If you have any questions or concerns please don't hesitate to get in touch!
Jon Pienkowski
Pacific NorthWest Computers
www.pnwcomputers.com
360-624-7379
Subscribe to:
Comments (Atom)


