With more than 20 years of experience, Pacific NorthWest Computers provides affordable on-site and in-shop computer repair services in Washington and Oregon State! We provide services ranging from onsite and remote support, malware removal, data recovery, laptop hardware repairs, custom-built computers, networking, security services, consulting/training, and many other computer/tech-related support and services! www.linktr.ee/pnwcomputers
Showing posts with label ransomware. Show all posts
Showing posts with label ransomware. Show all posts
Wednesday, November 2, 2022
Monday, March 7, 2022
Ransomware Infection? This could help!!
Ransomware infections are a very real and very serious problem that general computer users, and businesses alike, should be prepared for!
- First off, the best prevention to start with is to have good security software installed that can protect you from Ransomware infections (such as Malwarebytes Anti-malware, Kaspersky Antivirus, etc).
- Secondly, have a good data backup system in place that follows the 3-2-1 backup rule to keep your data safe!
- The 3-2-1 backup rule simply states that you should have:
- 3 copies of your data (your main data and 2 backup copies)
- On two different media types (NAS drive and a thumb drive)
- With one copy off-site for disaster recovery (cloud backup, etc).
If you do get hit with a ransomware infection, the website below can help you identify which ransomware you were infected with and if there is a de-encryption tool available to help get your data/files back: https://id-ransomware.malwarehunterteam.com/
Pacific NW Computers
www.pnwcomputers.com
360.624.7379
Labels:
antivirus,
bug,
clean my pc,
computer,
computer security,
infection,
malware,
microsoft,
new,
operating system,
protection,
ransom,
ransomware,
security,
update,
upgrade,
Virus,
windows,
windows 10,
windows 11
Monday, January 21, 2019
RansomWare or a Fake Tech Scammer Locked You Out of Your Computer using a "SysKey" Password
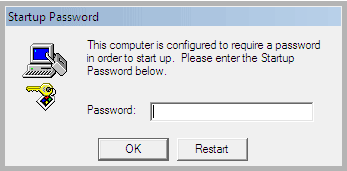
Some RansomWare Viruses and "Microsoft Tech" Scammers will Enable Windows' "SysKey" Function,
and lock you out of your computer!
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
*THIS IS FOR WINDOWS 7; MAY WORK ON 8 or 10 BUT THIS IS NOT TESTED OR CONFIRMED.
If this happens to you, the first thing you can try is use a Windows OS Media disk to remove the "SysKey" function using the Command Line.
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
- Boot to the appropriate OS Media (matches the installed OS version of the computer you are fixing).
- When the OS installation screen comes up, Select USA English and then "Repair the Windows Installation"; DO NOT INSTALL!!
- Go to "Advanced Troubleshooting"
- Click on "Advanced Repairs"
- Click on and open the the "Command Line" tool
- Find the OS Disk by changing drive letters and checkin contents with the "dir" command. ie: cd C: cd D: cd E:, etc.
- Run the following command on the OS drive:
copy c:\windows\system32\config\regback c:\windows\system32\config - Say no to the "Software" replace prompt, but say yes to the others and replace a total of 4 files; Default, SAM, Security and System.
- Reboot system
A warning however, you may have some security, OS and/or user account damage after the fact.
However there is an alternate method (or two) that can also do the trick, if the above process does not work, or is too difficult!
I have also removed the "Syskey" password using the following procedure:- Boot from a Windows 7 Install DVD/Thumbdrive, or boot from a user created Windows Restore/Repair Thumb Drive.
*You can also attempt the same procedure from Windows Start-Up Repair; if you are able to get there. - When the "Install Windows" screen appears, click on "Repair your computer" to access the system recovery options.
- From the nex screen, run System Restore to last point before the syskey password on your computer.
*This will fail, but must be done! - Click "run system restore again" and this will take you back to the main system recovery options list.
- Open Command Prompt from the main system recovery options list.
- Open Regedit; type "regedit" without the quotes, into the command prompt and the Regedit application will open.
- Navigate to: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa and change the 'SecureBoot' value entry from 1 to 0.
- Navigate to: HKEY_LOCAL_MACHINE \SAM\SAM\Domains\Account and delete everything for "F value" so that it's data/value is 0000
- Reboot and you should now be able to Login!
If you are not able to boot into the Windows 8 or 10 Startup Recovery Environment there is still yet another repair method you can try!
To get the computer to run a system restore if you can't get into the recovery environment, you try to make/trip the computer into doing a Startup Repair.- The way we do this, is by turning the system off mid boot and then Startup Repair should catch that "issue" and run the next time you power on.
- During this process Windows typically recommends running a system restore to fix any possible boot issues; allow this process to proceed and complete.
- After this process has completed, open the computer's DVD drive and insert a copy of Hiren's All-in-one Boot CD/thumb drive.
- Turn the system off/restart the system.
- Booting from DVD or USB, boot into the Hiren's All-in-one Media and select "Mini XP Recovery Environment"
- Allow your system to boot into the "Mini XP Recovery Environment" RAM Drive environment.
- Once booted into "Mini XP" you can now run the built in Registry Editor (regedit) to complete the registry edits needed and listed in the previous repair steps.
These all have worked for me on client machines and has allowed me to get passed a "syskey" password each time. Once I am able to login to the client's system, I will physically disconnect the internet and start my cleaning procedures on the affected system. After a full clean-up, software removal and tune-up the once locked PC will now run fine without the user getting locked out anymore!
I hope this helps general users or other IT professionals!
Pacific Northwest Computers
Jon Pienkowski - Owner/Operator
www.pnwcomputers.com
360.624.7379
Labels:
computer,
extortion,
fake tech support,
hack,
hackers,
locked out,
online scam,
password,
pc,
ransomware,
scam,
scammers,
syskey,
tech scam,
Virus
Tuesday, September 19, 2017
Ransomware; What You Need To Know
With the popularity of the "WannaCry" ransomware bug that went around in early 2017, most folks are pretty familiar with the term Ransomware (aka an extortion virus). If you are not familiar with term, essentially a Ransomware virus is bug that usually gets into a system through an infected attachment via a fake Email. Once the email is opened, the virus activates and immediately starts to seek out and encrypt Word Documents, Excel Spreadsheets, Pictures, Music; anything it can get it's hands on. It is a VERY destructive type of attack and if not prepared, you could loose all of the precious data that is stored on your computer and connected to your computer!
So what is Data Encryption?
Data encryption is a way to lock a file, or any type of data on a hard drive, very securely. Encryption essentially locks a file with a nearly unbreakable secret password, key, etc. Once a file has been "locked" or encrypted, you need have to have the secret key or password to be able unlock and access file(s) again. The key or password is what enables you to decrypt, or "unlock" the file, and have access to all your stuff again; pictures, documents, music, etc. So what the scammers are trying to achieve with deploying Ransomware is to lock your data up and then extort money from you to get your data back. Essentially make you pay a ransom to get your data unlocked and accessible again.What can you do to protect yourself from Ransomware attacks?
- BACKUP YOUR DATA: Back up your files remotely every day, but only on a hard drive that is not connected to the internet. So long as you back up files on an external hard drive, you won’t lose any information if hit by a ransomware attack.
- NEVER OPEN A SUSPICIOUS EMAIL ATTACHMENT: And never download an app that you haven’t verified with an actual store. Read reviews before installing programs.
- SCAN ALL DOWNLOADS: Some antivirus programs have the ability to scan files to see if they might contain ransomware. Make use of them before downloading any questionable attachments from email or software from the internet.
- EXTRA PROTECTION: If you want take things a step even further, BitDefender does have an Anti-Ransomware security tool you can install and run on your computer to supplement (and work in conjunction with) your existing security software:
www.bitdefender.com/solutions/anti-ransomware-tool.html
What do you do if you have already gotten infected with Ransomware?
If your computer has been attacked by ransomware, you can explore the free ransomware response kit (from ZDNet) for a suite of tools that can help with a ransomware attack.Pacific Northwest Computers also recommends the following to moderate an attack as well:
- Remove the infected machines from the network, so the ransomware does not use the machine to spread throughout your network!! VERY IMPORTANT!!
- Decide whether or not to restore from available backups, try to decrypt the encrypted data, or pay the ransom and take it as a lesson learned.
- Research if similar malware has been investigated by other IT teams, and if it is possible to decrypt it on your own. About 30 percent of encrypted data can be decrypted without paying a ransom. Some of those tools are listed below:
- esupport.trendmicro.com/en-us/home/pages/technical-support/1114221
- www.avast.com/ransomware-decryption-tools
- www.avg.com/en-us/ransomware-decryption-tools
- noransom.kaspersky.com
- decrypter.emsisoft.com
- More Tools: www.thewindowsclub.com/list-ransomware-decryptor-tools
If the none of the available decryption tools work (or a decryption tool is not available for your specific type or Ransomware) data recovery could be a last resort option. There have been cases where when the Ransomware virus attacks and the data encryption first occurs, the original file is actually copied and then deleted, and the copied file is what gets's encrypted! So we can try to recover those original files!
If you have been hit by a Ransomware virus, you need Ransomware Data Recovery, or you are interested in getting some systems in place to be prepared and protected in the case of a Ransomware attack, feel free to reach out to us!
Pacific Northwest Computers
Pacific Northwest Computers
Jon Pienkowski ~ Owner/Operator
360.624.7379
Jon Pienkowski ~ Owner/Operator
Labels:
antivirus,
attack,
Crypto,
Data,
data backup,
data recovery,
Decrypt,
locky,
protection,
ransom,
ransomware,
Virus,
virus removal,
wannacry
Monday, May 15, 2017
WannaCry Ransomware Virus
The now infamous "WannaCry" ransom-ware virus has been making headlines and scaring a lot of computer users around the world. It is one of the quickest spreading Ransom-ware bugs that has been released to date, but Ransom-ware viruses are not anything new.
Ransom-ware viruses are a type of virus that infect computers, and then prevent the user from accessing the operating system, or encrypting all the data stored on the computer. Then the user is asked to pay a fixed amount of money as ransom to unlock their files, allowing them to regain access to the operating system and their data again. What sets this virus apart is how quickly and widely it has spread.
As of yesterday a Security Professional, Marcus Hutchins, has been credited with stopping the WannaCry ransomware attack from spreading across the globe, by accidentally triggering a "kill switch" found in reverse engineering the virus. So for now, further infection has been stopped. But to prevent any infections from previous distributions of the bug you can do the following:
"WannaCry" Ransomware Guidelines to Stay Safe:
- Be careful to NOT click on harmful links in your emails!
- Even with security software installed, if you open/download an attachment from a malicious email it can and will infect a computer and network!
- If you get an email from someone, look at the email address/email header and make sure it's from who it says it is.
- Be aware of fraudulent e-mail messages that use names similar to popular services such as PayPal instead of PayPal or use popular service names without commas or excessive characters.
- Be wary of visiting unsafe or unreliable sites
- Never click on a link that you do not trust on a web page or access to Facebook or messaging applications such as WatSab and other applications.
- If you receive a message from your friend with a link, ask him before opening the link to confirm, (infected machines send random messages with links).
- Always make have the latest update for your Antivirus; Let me know if there are any update issues!
- Make sure your windows have the latest updates to close the gap!
- If windows has reported that updates are pending/available; download and install immediately!!
- Make a recovery disk! The WannaCry ransomware asks for $300 or more if you a modified version if you do not pay the creators (in Bitcoin to its untraceable and not refundable) encrypt all of your files on the computer.
- If your computer gets infected take it off of your network immediately! The ransomware will spread to other computers on the network! You can restore from a backup.
- If you would like our assistance with ANY of the procedures above or would like us to secure your computer and/or network to the best of it's ability, let us know and we can schedule an onsite or remote session for you!!
More from Microsoft on the bug and associated patches to help prevent infections from WannaCry:
https://technet.microsoft.com/…/libr…/security/ms17-010.aspx
Jon-Eric Pienkowski
_________________________
Pacific NorthWest Computers
(360) 624-7379
Subscribe to:
Comments (Atom)



