At Pacific NorthWest Computers, we don't have any monthly-fee type services or anything like that, as we don't provide "help desk style support".
But, we are preferred/dedicated IT provider for a lot of businesses in the area on a "call us as needed" basis!
How it typically works is we will schedule quarterly clean-up visits to check hardware, backups, check for bugs and perform software/OS updates; as well as address specific issues that you may be happening.
With this business model, we have helped nearly all of our business clients cut out HUGE monthly IT support bills, as well as provide a higher quality, and personable, level of care and support. We recently got a client out of a nearly $500 a month IT service contract, down to maybe spending $160-$300 every three months. That is a nearly 80% decrease in total IT costs just by switching over to us!
If your business is interested in cutting down on, and/or completely eliminating, bloated and overpriced IT support services, give Pacific Northwest Computers a call today!
www.pnwcomputers.com
360.624.7379
With more than 16 years of experience, Pacific NorthWest Computers provides affordable on-site and in-shop computer repair services in the Washington and Oregon State! We provide services ranging from onsite and remote support, malware removal, data recovery, laptop hardware repairs, custom built computers, networking, security services, consulting/training, and a plethora of other computer/tech related support and services! www.linktr.ee/pnwcomputers
Wednesday, August 21, 2019
Tuesday, May 14, 2019
Can People Easily Find Your Business?
Can People Easily Find Your Business?
Is your Business listed on the major sales/services directory sites?
Do you have a social media presence; not just for followers but just to be found by their users?
Can users of different social, community, and information sites easily find you?
Clickfunnels, landing pages, blogs; do you need to implement all of those? Some of them? None of them?
Pacific NorthWest Computers can not only help more people find your company, product, or service but ALSO help search engines find pertinent info and data, all while building an Organic SEO system that runs on autopilot; helping increase your rankings, exposure, conversations, sales, profits, etc. With all of that in place, advertising is a piece of cake!
We then can help you INTELLIGENTLY use Google AdSense, Facebook Advertising, and Instagram Advertising using tools like Google Business, Google Search Console, and Google Analytics to intelligently approach and ATTACK your advertising campaigns. Get impressions, get those clicks, get those conversions and get those profits that have just been slipping by!
Interested? Setup a consult today!
Pacific Northwest Computers
www.pnwcomputers.com
360.624.7379
Jon@pnwcomputers.com
Only $100 per hour, and we can cover a LOT of ground in just an hour or two!!
Is your Business listed on the major sales/services directory sites?
Do you have a social media presence; not just for followers but just to be found by their users?
Can users of different social, community, and information sites easily find you?
Clickfunnels, landing pages, blogs; do you need to implement all of those? Some of them? None of them?
Pacific NorthWest Computers can not only help more people find your company, product, or service but ALSO help search engines find pertinent info and data, all while building an Organic SEO system that runs on autopilot; helping increase your rankings, exposure, conversations, sales, profits, etc. With all of that in place, advertising is a piece of cake!
We then can help you INTELLIGENTLY use Google AdSense, Facebook Advertising, and Instagram Advertising using tools like Google Business, Google Search Console, and Google Analytics to intelligently approach and ATTACK your advertising campaigns. Get impressions, get those clicks, get those conversions and get those profits that have just been slipping by!
Interested? Setup a consult today!
Pacific Northwest Computers
www.pnwcomputers.com
360.624.7379
Jon@pnwcomputers.com
Only $100 per hour, and we can cover a LOT of ground in just an hour or two!!
Monday, January 21, 2019
RansomWare or a Fake Tech Scammer Locked You Out of Your Computer using a "SysKey" Password
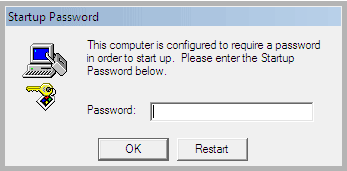
Some RansomWare Viruses and "Microsoft Tech" Scammers will Enable Windows' "SysKey" Function,
and lock you out of your computer!
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
*THIS IS FOR WINDOWS 7; MAY WORK ON 8 or 10 BUT THIS IS NOT TESTED OR CONFIRMED.
If this happens to you, the first thing you can try is use a Windows OS Media disk to remove the "SysKey" function using the Command Line.
Well we have a few ways you can remove that pesky "SysKey,
and get you back into your computer!
- Boot to the appropriate OS Media (matches the installed OS version of the computer you are fixing).
- When the OS installation screen comes up, Select USA English and then "Repair the Windows Installation"; DO NOT INSTALL!!
- Go to "Advanced Troubleshooting"
- Click on "Advanced Repairs"
- Click on and open the the "Command Line" tool
- Find the OS Disk by changing drive letters and checkin contents with the "dir" command. ie: cd C: cd D: cd E:, etc.
- Run the following command on the OS drive:
copy c:\windows\system32\config\regback c:\windows\system32\config - Say no to the "Software" replace prompt, but say yes to the others and replace a total of 4 files; Default, SAM, Security and System.
- Reboot system
A warning however, you may have some security, OS and/or user account damage after the fact.
However there is an alternate method (or two) that can also do the trick, if the above process does not work, or is too difficult!
I have also removed the "Syskey" password using the following procedure:- Boot from a Windows 7 Install DVD/Thumbdrive, or boot from a user created Windows Restore/Repair Thumb Drive.
*You can also attempt the same procedure from Windows Start-Up Repair; if you are able to get there. - When the "Install Windows" screen appears, click on "Repair your computer" to access the system recovery options.
- From the nex screen, run System Restore to last point before the syskey password on your computer.
*This will fail, but must be done! - Click "run system restore again" and this will take you back to the main system recovery options list.
- Open Command Prompt from the main system recovery options list.
- Open Regedit; type "regedit" without the quotes, into the command prompt and the Regedit application will open.
- Navigate to: HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Lsa and change the 'SecureBoot' value entry from 1 to 0.
- Navigate to: HKEY_LOCAL_MACHINE \SAM\SAM\Domains\Account and delete everything for "F value" so that it's data/value is 0000
- Reboot and you should now be able to Login!
If you are not able to boot into the Windows 8 or 10 Startup Recovery Environment there is still yet another repair method you can try!
To get the computer to run a system restore if you can't get into the recovery environment, you try to make/trip the computer into doing a Startup Repair.- The way we do this, is by turning the system off mid boot and then Startup Repair should catch that "issue" and run the next time you power on.
- During this process Windows typically recommends running a system restore to fix any possible boot issues; allow this process to proceed and complete.
- After this process has completed, open the computer's DVD drive and insert a copy of Hiren's All-in-one Boot CD/thumb drive.
- Turn the system off/restart the system.
- Booting from DVD or USB, boot into the Hiren's All-in-one Media and select "Mini XP Recovery Environment"
- Allow your system to boot into the "Mini XP Recovery Environment" RAM Drive environment.
- Once booted into "Mini XP" you can now run the built in Registry Editor (regedit) to complete the registry edits needed and listed in the previous repair steps.
These all have worked for me on client machines and has allowed me to get passed a "syskey" password each time. Once I am able to login to the client's system, I will physically disconnect the internet and start my cleaning procedures on the affected system. After a full clean-up, software removal and tune-up the once locked PC will now run fine without the user getting locked out anymore!
I hope this helps general users or other IT professionals!
Pacific Northwest Computers
Jon Pienkowski - Owner/Operator
www.pnwcomputers.com
360.624.7379
Labels:
computer,
extortion,
fake tech support,
hack,
hackers,
locked out,
online scam,
password,
pc,
ransomware,
scam,
scammers,
syskey,
tech scam,
Virus
Thursday, January 10, 2019
Make 802.11ac Work Correctly On A Linksys WRT1900AC
Make 802.11ac Work Correctly On A Linksys WRT1900AC Router
I have had a Linksys WRT1900AC router for quiet sometime now, and in it's name it says that is an AC router. Since I have AC compatible Wifi devices, theoretically I should be able to get a max speed of around 1300 Mbps. In reality it would likely see something around 600 Mbps to something around 1024 Mbps due to the connections being wireless and can have interference. What I recently discovered though was that I was getting 802.11n speeds on my devices. I found that to be weird. So I checked the route's settings.
Under "Network Mode" in the router's settings (logged in through a browser via the router's IP address), I found that the only options for wireless network modes were for A, N or A/N. But nowhere in the menus/options does it specify an option for 802.11ac!?
That was baffling to me seeing as this router is capable of doing 802.11ac according to Linksys AND it's in the devices NAME. So I figured that I was doing something wrong or I was not looking in the right place. Naturally, I checked their FAQ section and found nothing on this.
I also did what I tell ALL my customers to do and read the manual; found no assistance there.
After doing someone line research I found that if flipped the setting in "Network Mode from A/N only to Mixed (and after a reboot of the router) I had 802.11ac speeds! This router apparently HAS to be on "Mixed Mode" for AC speeds to be achieved. Very odd that Linksys would NOT include an AC option in the "Network Mode" section in the router settings, or make it more clear the A/N mode disables/prevents AC speeds all together.
Since I was able to figure it out, I wanted to make this post to hopefully help folks out that find themselves with the same or similar issue!
Pacific Northwest Computers
www.pnwcomputers.com
360.624.7379
Labels:
5ghz,
802.11,
ac,
adapter,
gbps,
home network,
home wifi,
lan,
linksys,
mbps,
network,
network speed,
networking,
router,
speed,
wifi,
wireless,
wireless networking,
wireless router,
wrt1900ac
Monday, May 7, 2018
Identify and Remove Un-needed Programs from your PC or Mac!
Ever wonder how to clean out your computer? Many people do, because it’s not unusual to have your PC filled with adware, toolbars and other programs you no longer need or probably never intended to install in the first place. But like most people, what programs should you remove is the tough question.
Well we have your answer!
For PC users, you just simply need to visit and download "Should I Remove It?"! "Should I Remove It?" is a tiny, lightweight program designed to show you what programs you have installed on your computer and quickly determine what programs you can safely remove.
For an even deeper clean, we can't recommend CCleaner enough! CCleaner can help restore your system speed by removing unnecessary files taking up room on your hard drive as well as clear out errors and broken settings to improve stability. CCleaner can also help boost your browser speed and help protect your privacy by securely erasing tracking cookies and history!
Now, for the Apple Computers, there is CleanMyMac.com. CleanMyMac finds the junk that got installed on your Mac and full system cleaning. It helps you figure out if your system has extra/unneeded add-ons installed and even left over junk files from old programs and software/system upgrades. When everything on your Mac works twice as fast, you accomplish more every day. All you need is the right tool to make your Mac clean and fast again. CleanMyMac is perfect for the job: it removes the clutter from hard drive and speeds up your system. Plus, it’s super easy to use!
Should I Remove It? ~ www.shouldiremoveit.com <-- clean-up="" div="" program="" windows="">
CCleaner ~ www.ccleaner.com <-- cleaning="" deep="" div="" program="" windows="">
CleanMyMac ~ www.cleanmymac.com <-- app="" clean-up="" div="" macintosh="">
Pacific Northwest Computers
www.pnwcomputers.com
Labels:
adware,
applications,
bloatware,
ccleaner,
clean,
clean my computer,
clean my mac,
clean my pc,
faster,
pc,
piriform,
programs,
shouldiremoveit,
speed up,
tune up,
uninstall,
windows
Monday, March 12, 2018
Run macOS in Windows via Virtual Machine!
With a few downloads, a hand full of steps to follow, you can have a Virtual Apple computer running on your Windows PC. That's right! Your eyes are not deceiving you. You can create a macOS virtual machine using VMware Workstation Player! Have access to the apps, tools, programs that you love about your Apple computer, all on your Windows PC!! No "hackintosh" required.
The link for the tutorial is below and will require you to download and install several programs as well as modify a config file using NotePad. Nothing crazy, but there are quiet a few steps involved. So read carefully and pay close attention to each step.
Link: Run macOS High Sierra OSX via Virtual Machine on a Windows PC!
**A few quick notes regarding this guide!**
- VMware Virtual Workstation Player us up to version 14. However the needed "unlocker" utility that makes VMware Workstation Player compatible with OSX is ONLY compatible with copies of Version 12 VMware Virtual Workstation Player. So DO NOT download the newest version of VMware Virtual Workstation Player; only use copies of version 12.
- You DO NOT need an ISO or currently OSX installation media. The tutorial has a link to have to download the Intel version of the Mac OSX virtual machine. This virtual machine is provided courtesy of the excellent fellows at Techsvidrewer.
Thank you PCSteps.com for creating such an easy to follow and thorough setup/install guide!!
Pacific Northwest Computers
www.pnwcomputers.com
Labels:
apple,
computers,
hackintosh,
high sierra,
imac,
ISO,
mac,
macbook pro,
microsoft,
os,
osx,
pacific,
pacific northwest,
pc,
pnw computers,
pnwcomputers,
virtual,
virtual machine,
vmware,
windows
Friday, January 12, 2018
Cryptocurrency GPU Mining Rig Parts List
Basic Parts List for a GPU Cryptocoin Mining Rig:
- *GIGABYTE GA-H110-D3A Cryptocurrency Mining ATX Motherboard
or... - *Biostar 189846 Motherboard
- **Intel BX80677G3930 7th Gen Celeron Desktop Processor
- Patriot Signature 4GB DDR3 PC3-12800 (1600MHz)
- ***DREVO X1 Pro 64GB SSD Internal Solid State Drive 2.5-Inch SATA3
- ****Cooler Master V1200 - Fully Modular 1200W 80 PLUS Platinum PSU
- Electop 3 Pack - 2 Pin PC Power Switch Cable Momentary on/off Push Button Cable
- Leboo 6-Pack 6 PIN 1x to x16 Powered Riser Adapter Card w/ 60cm USB 3.0 Extension Cable & PCI-E to SATA Power Cable
- Electop 2 Pack Super Speed USB 3.0 Right Angle Male to Female 90 Degree Connector
- ASUS Radeon RX 580 8GB Dual-fan OC Edition GDDR5
Example Hash Rates for Various Video Cards:
*The goal with your motherboard is to have as many PCIe 1x and 16x slots as you can get!
**You can also go with Pentium-Dual core or any other low-cost/low-power CPU's.
***You can use a high-speed thumb drive instead of a SSD or standard HDD if you are going to be using a Linux or any "small footprint" mining software/distro.
****You can go with any 1000+ Watt PSU as long as it is at least Gold/Platinum 80+ Certified.
Tuesday, September 19, 2017
Ransomware; What You Need To Know
With the popularity of the "WannaCry" ransomware bug that went around in early 2017, most folks are pretty familiar with the term Ransomware (aka an extortion virus). If you are not familiar with term, essentially a Ransomware virus is bug that usually gets into a system through an infected attachment via a fake Email. Once the email is opened, the virus activates and immediately starts to seek out and encrypt Word Documents, Excel Spreadsheets, Pictures, Music; anything it can get it's hands on. It is a VERY destructive type of attack and if not prepared, you could loose all of the precious data that is stored on your computer and connected to your computer!
So what is Data Encryption?
Data encryption is a way to lock a file, or any type of data on a hard drive, very securely. Encryption essentially locks a file with a nearly unbreakable secret password, key, etc. Once a file has been "locked" or encrypted, you need have to have the secret key or password to be able unlock and access file(s) again. The key or password is what enables you to decrypt, or "unlock" the file, and have access to all your stuff again; pictures, documents, music, etc. So what the scammers are trying to achieve with deploying Ransomware is to lock your data up and then extort money from you to get your data back. Essentially make you pay a ransom to get your data unlocked and accessible again.What can you do to protect yourself from Ransomware attacks?
- BACKUP YOUR DATA: Back up your files remotely every day, but only on a hard drive that is not connected to the internet. So long as you back up files on an external hard drive, you won’t lose any information if hit by a ransomware attack.
- NEVER OPEN A SUSPICIOUS EMAIL ATTACHMENT: And never download an app that you haven’t verified with an actual store. Read reviews before installing programs.
- SCAN ALL DOWNLOADS: Some antivirus programs have the ability to scan files to see if they might contain ransomware. Make use of them before downloading any questionable attachments from email or software from the internet.
- EXTRA PROTECTION: If you want take things a step even further, BitDefender does have an Anti-Ransomware security tool you can install and run on your computer to supplement (and work in conjunction with) your existing security software:
www.bitdefender.com/solutions/anti-ransomware-tool.html
What do you do if you have already gotten infected with Ransomware?
If your computer has been attacked by ransomware, you can explore the free ransomware response kit (from ZDNet) for a suite of tools that can help with a ransomware attack.Pacific Northwest Computers also recommends the following to moderate an attack as well:
- Remove the infected machines from the network, so the ransomware does not use the machine to spread throughout your network!! VERY IMPORTANT!!
- Decide whether or not to restore from available backups, try to decrypt the encrypted data, or pay the ransom and take it as a lesson learned.
- Research if similar malware has been investigated by other IT teams, and if it is possible to decrypt it on your own. About 30 percent of encrypted data can be decrypted without paying a ransom. Some of those tools are listed below:
- esupport.trendmicro.com/en-us/home/pages/technical-support/1114221
- www.avast.com/ransomware-decryption-tools
- www.avg.com/en-us/ransomware-decryption-tools
- noransom.kaspersky.com
- decrypter.emsisoft.com
- More Tools: www.thewindowsclub.com/list-ransomware-decryptor-tools
If the none of the available decryption tools work (or a decryption tool is not available for your specific type or Ransomware) data recovery could be a last resort option. There have been cases where when the Ransomware virus attacks and the data encryption first occurs, the original file is actually copied and then deleted, and the copied file is what gets's encrypted! So we can try to recover those original files!
If you have been hit by a Ransomware virus, you need Ransomware Data Recovery, or you are interested in getting some systems in place to be prepared and protected in the case of a Ransomware attack, feel free to reach out to us!
Pacific Northwest Computers
Pacific Northwest Computers
Jon Pienkowski ~ Owner/Operator
360.624.7379
Jon Pienkowski ~ Owner/Operator
Labels:
antivirus,
attack,
Crypto,
Data,
data backup,
data recovery,
Decrypt,
locky,
protection,
ransom,
ransomware,
Virus,
virus removal,
wannacry
Monday, May 15, 2017
WannaCry Ransomware Virus
The now infamous "WannaCry" ransom-ware virus has been making headlines and scaring a lot of computer users around the world. It is one of the quickest spreading Ransom-ware bugs that has been released to date, but Ransom-ware viruses are not anything new.
Ransom-ware viruses are a type of virus that infect computers, and then prevent the user from accessing the operating system, or encrypting all the data stored on the computer. Then the user is asked to pay a fixed amount of money as ransom to unlock their files, allowing them to regain access to the operating system and their data again. What sets this virus apart is how quickly and widely it has spread.
As of yesterday a Security Professional, Marcus Hutchins, has been credited with stopping the WannaCry ransomware attack from spreading across the globe, by accidentally triggering a "kill switch" found in reverse engineering the virus. So for now, further infection has been stopped. But to prevent any infections from previous distributions of the bug you can do the following:
"WannaCry" Ransomware Guidelines to Stay Safe:
- Be careful to NOT click on harmful links in your emails!
- Even with security software installed, if you open/download an attachment from a malicious email it can and will infect a computer and network!
- If you get an email from someone, look at the email address/email header and make sure it's from who it says it is.
- Be aware of fraudulent e-mail messages that use names similar to popular services such as PayPal instead of PayPal or use popular service names without commas or excessive characters.
- Be wary of visiting unsafe or unreliable sites
- Never click on a link that you do not trust on a web page or access to Facebook or messaging applications such as WatSab and other applications.
- If you receive a message from your friend with a link, ask him before opening the link to confirm, (infected machines send random messages with links).
- Always make have the latest update for your Antivirus; Let me know if there are any update issues!
- Make sure your windows have the latest updates to close the gap!
- If windows has reported that updates are pending/available; download and install immediately!!
- Make a recovery disk! The WannaCry ransomware asks for $300 or more if you a modified version if you do not pay the creators (in Bitcoin to its untraceable and not refundable) encrypt all of your files on the computer.
- If your computer gets infected take it off of your network immediately! The ransomware will spread to other computers on the network! You can restore from a backup.
- If you would like our assistance with ANY of the procedures above or would like us to secure your computer and/or network to the best of it's ability, let us know and we can schedule an onsite or remote session for you!!
More from Microsoft on the bug and associated patches to help prevent infections from WannaCry:
https://technet.microsoft.com/…/libr…/security/ms17-010.aspx
Jon-Eric Pienkowski
_________________________
Pacific NorthWest Computers
(360) 624-7379
Wednesday, April 12, 2017
Security & Performance for your PC!!
I get asked all the time, “Jon, what do you recommend for security and performance for my computer?” So I decided to give folks a brief, and to the point, run down of what I programs and tools I use and recommend.
So, core security: I typically use and install Avast Free or BitDefender Free Antivirus (MS Security if Windows 7). Then I always use (and have used for years) MalwareBytes Antimalware and Spybot Search & Destroy. MalwareBytes is a Zero-day exploit and “name brand” bug catcher King and Spybot can find a lot of stuff that normally would get left behind and can also undo damage a virus has caused to your system. But you do not want them to be running all the time, as your Antivirus is providing that protection. MBAM (MalwareBytes for short) and Spybot are just "tools in the toolbox" per say. Include them in your routine scans and cleanings but they will be your go to, if and when a virus gets around your Antivirus. But the basic "run it when you need it" free versions are all you need (unless you have computer with horsepower and speed then let em rip!).
Then with the new variant of malware being “browser hi-jack” bugs, if you get hit with something like that, all those other security programs may not be able to find all of them; or even any of them at all! So that is where ADWCleaner and JRT come in to play. Both are now distributed by MalwareBytes (so that's who you will likely download them from as an FYI), they are specifically browser hi-jack clean-up tools. These tools will find, fix and remove what the other programs cant. Including website re-directions, search engine and homepage hi-jacks, removal of malicious add-ons, and much more.
Then last but not least, lets keep the computer clean of junk!
CCleaner has been my go-to performance and clean-up tool for nearly my entire professional computer career. Junk, temp and cache files, prefetch data, DNS cache, delete free space; CCleaner can do A LOT! So to keep things clean and your computer running snappy, I highly recommend it’s installation and use!
You can find direct download links to all the previously mentioned programs, as well as a complete virus removal tutorial just by clicking the link below! Doesn’t get much easier than that ;)
Recommended Software Downloads & Virus Removal Tutorial
As always, if you need any kind of computer or “tech” help, or if you have any questions, feel free to get in touch! This is why I do, what I do :)
Jon Pienkowski
So, core security: I typically use and install Avast Free or BitDefender Free Antivirus (MS Security if Windows 7). Then I always use (and have used for years) MalwareBytes Antimalware and Spybot Search & Destroy. MalwareBytes is a Zero-day exploit and “name brand” bug catcher King and Spybot can find a lot of stuff that normally would get left behind and can also undo damage a virus has caused to your system. But you do not want them to be running all the time, as your Antivirus is providing that protection. MBAM (MalwareBytes for short) and Spybot are just "tools in the toolbox" per say. Include them in your routine scans and cleanings but they will be your go to, if and when a virus gets around your Antivirus. But the basic "run it when you need it" free versions are all you need (unless you have computer with horsepower and speed then let em rip!).
Then with the new variant of malware being “browser hi-jack” bugs, if you get hit with something like that, all those other security programs may not be able to find all of them; or even any of them at all! So that is where ADWCleaner and JRT come in to play. Both are now distributed by MalwareBytes (so that's who you will likely download them from as an FYI), they are specifically browser hi-jack clean-up tools. These tools will find, fix and remove what the other programs cant. Including website re-directions, search engine and homepage hi-jacks, removal of malicious add-ons, and much more.
Then last but not least, lets keep the computer clean of junk!
CCleaner has been my go-to performance and clean-up tool for nearly my entire professional computer career. Junk, temp and cache files, prefetch data, DNS cache, delete free space; CCleaner can do A LOT! So to keep things clean and your computer running snappy, I highly recommend it’s installation and use!
You can find direct download links to all the previously mentioned programs, as well as a complete virus removal tutorial just by clicking the link below! Doesn’t get much easier than that ;)
Recommended Software Downloads & Virus Removal Tutorial
As always, if you need any kind of computer or “tech” help, or if you have any questions, feel free to get in touch! This is why I do, what I do :)
Jon Pienkowski
Pacific Northwest Computers
360.624.7379
Subscribe to:
Posts (Atom)





