With more than 20 years of experience, Pacific NorthWest Computers provides affordable on-site and in-shop computer repair services in Washington and Oregon State! We provide services ranging from onsite and remote support, malware removal, data recovery, laptop hardware repairs, custom-built computers, networking, security services, consulting/training, and many other computer/tech-related support and services! www.linktr.ee/pnwcomputers
Tuesday, March 5, 2024
Scan/Repair Corrupted Windows 10 & Windows 11 System Files
Monday, January 15, 2024
Lenovo Legion Y740 Series Keyboard Issues
Lenovo Legion Y740 Series Keyboard Issues
Links to the needed firmware update(s) to fix Lenovo Legion Y740 series RGB keyboard functionality/stops working issues.
Firmware Software Needed: kyb17fw03u
Lenovo Legion Y740 Series 15" Model:
https://download.lenovo.com/consumer/mobiles/kyb15fw02u/kyb15fw02u.exe
Lenovo Legion Y740 Series 17" Model:
https://download.lenovo.com/consumer/mobiles/kyb17fw02u/kyb17fw02u.exe
Thursday, October 19, 2023
How To Protect Yourself From Scammers
How To Protect Yourself From Scammers
Scammers are versatile in their tactics, posing as various entities, including banks, real estate agencies, utility companies, and even family members or government agencies. They often employ pressure tactics to create a false sense of urgency, leading to rushed decisions and financial losses. To safeguard your interests, it's essential to be vigilant and take proactive steps to prevent falling victim to scams. This article offers insights and tips on how to protect yourself from scammers.
Question Too-Good-To-Be-True Offers
Be Wary of "Grandparent Scams"
Guard Your Passwords and PINs
Protect Against Phishing Emails
Implement Security Best Practices
- Be Cautious with Money Transfers:
- Avoid sending money to individuals you don't know in real life, particularly through third-party services like Zelle, Venmo, and Cash App.
- Refrain from using gift cards to settle bills; legitimate businesses do not request payment via gift cards.
- Ignore Unsolicited Messages:
- Delete random texts and emails that ask you to click a link or provide personal information.
- Never click on links from untrusted sources.
- Regularly Monitor Your Accounts:
- Stay vigilant by regularly monitoring your financial accounts.
- Respond promptly to fraud alerts and report any unauthorized transactions.
Enable Multifactor Authentication
Understanding Fake Websites and How Scammers Exploit Them
Recognizing fake websites is becoming increasingly challenging. To ensure you're not dealing with a fraudulent website, remain vigilant and apply the aforementioned protection measures. By staying informed and exercising caution, you can significantly reduce your vulnerability to scams and safeguard your online security.
In conclusion, being proactive, skeptical, and informed is the best defense against scammers. Protect your personal and financial information by following these guidelines, and remember that it's always better to be cautious than to fall victim to fraudulent schemes.
We Also Recommend Reading:
11 Ways To Spot a Fake Website
11 Ways To Spot a Fake Website
- Check the domain name closely:
The easiest way to tell that you’re on a fake website is when the domain name doesn’t match the official website of the company. For example, scammers often use domain names that are similar to, or even contain, the official URL within the fake domain name. - Look for a padlock symbol (but don’t trust it as a sole means of verification):
All web browsers (such as Safari, Firefox, and Google Chrome) show whether a site has what’s called a “security certificate.” This certificate (also known as an SSL certificate) verifies that any information you send to the site can’t be intercepted by hackers.
You can check if a site has a valid security certificate by looking for a padlock symbol by the URL in the address bar. (Again, make sure you’re on the correct page first.) - Use a website checker or safe browsing tools:
A website checker helps you answer if a website is safe to visit. For example, it tells you if the site uses encryption to protect your data, along with the site’s level of verification certificate. There are some good free resources that you can use to check if a website is safe to use. - Look for poor spelling, design issues, and other red flags:
Scammers move quickly and often don’t want to take too long to build fake websites (which could be identified as fraudulent and get taken down). Similar to scam emails and texts, phishing websites often include basic flaws and mistakes that legitimate companies wouldn’t miss. - Check the domain age (how long the site has been active):
Fake websites rarely stay online for long. One way to tell if a website is real or fake is to check how long it’s been active by using the Whois Lookup domain tracker.
Enter the website’s URL and you’ll be able to see details such as the owner’s organization name, country of registration, and domain age. It’s probably a fake website if the company claims to be registered in the United States, but their Whois Lookup query shows that they’re in another country."
Alternatively, you can try to use the Wayback Machine to see archived versions of the website and determine if it’s been used for multiple purposes. - Be wary of deals that seem too good to be true:
Scammers know you’re willing to set your suspicions aside for a good deal. When shopping online, don’t be fooled into trusting sketchy websites because you might save money. These fake shopping sites either steal your financial information or send you cheap knock-off versions of the items that you think you’re buying.
A good rule of thumb is that if a site advertises prices that are all +50% off, you should take steps to confirm it’s not a fake website. For example, verify it with a website checker, look for spelling and grammar mistakes, and check the domain age and information against what’s listed. - Look for user reviews, and check for reports of scams:
In an effort to look more legitimate, scammers often post fake reviews on their websites. But at the same time, real customers (who might have gotten scammed) can also write reviews warning you about their experiences. Read on- and off-site reviews for mentions of fraud, non-delivery, or even identity theft. While you’re checking reviews, see if anything feels off. Scammers often create fake bot accounts on review sites in order to build trust.
If there aren’t any reviews on the site, you can run a Google search for “Is [website name/URL] real/a scam?” The Better Business Bureau’s Scam Tracker website is also a great place to check for negative reviews about a company. - Read the shipping and return policy:
Official retailers have a dedicated webpage detailing their shipping and return policy. If the website you’re on doesn’t explain how to return an item, it’s a scam. The website should also include basic legal information, such as its terms and conditions, privacy policy, and data collection policy. If you can’t find this information, it’s likely not a legitimate company. - Scrutinize your payment options:
Fake websites sometimes try to force you to pay for goods using non-reversible or non-traceable payment methods; such as gift cards, bank transfers, cryptocurrencies, or payment apps like Zelle, Cash App, and Venmo. Legitimate brands will always give you the option of paying with more traditional and safer methods; including credit and debit cards, PayPal, or “buy now, pay later” options, such as Klarna and Afterpay. When in doubt, contact the issuing organization for the trust mark to verify the company's legitimacy. - Run a virus scan if you experience numerous ads and pop-ups:
Sometimes the goal of a fake website isn’t to steal your information, passwords, or money — but to infect your device with malware. Hackers create pop-ups and ad-riddled websites that can infect your phone or computer with viruses that let cybercriminals spy on you, scan your device for sensitive data, or lock your device until you pay a ransom. f you’ve been to a site like this recently, you need to make sure your device hasn’t been compromised.
December 13, 2022
Friday, August 18, 2023
Protect Your Comcast.net Email from Hijackers
How to Protect Your Comcast.net Email Account from Hijackers
If you use Comcast.net email, you may have heard of some cases where customers’ email accounts were hijacked by hackers. This can be a very frustrating and scary situation, as hackers can use your email account to scam your contacts, steal your personal information, or cause other damages.In this blog article, I will explain how hackers can hijack your Comcast.net email account, what they can do with it, and how you can protect yourself from this threat.
How Hackers Can Hijack Your Comcast.net Email Account
There are different ways that hackers can gain access to your Comcast.net email account, but one of the most common methods is phishing. Phishing is when hackers send you fake emails or direct you to fake websites that look like they are from Comcast or other legitimate sources. They may ask you to enter your email address and password or click on a link or attachment that contains malware. If you fall for their tricks, they can capture your login credentials and use them to access your email account.Another possible method that hackers can use to hijack your Comcast.net email account is through a data breach. A data breach is when hackers break into a database that contains sensitive information, such as email addresses and passwords. If the database belongs to Comcast or a third-party service that you use with your Comcast.net email account, hackers may be able to obtain your login credentials and use them to access your email account.
What Hackers Can Do With Your Comcast.net Email Account
Once hackers have access to your Comcast.net email account, they can do a lot of malicious things with it. Some of the common things that hackers can do are:- Set up email redirection or auto-forwarding rules. This means that hackers can forward emails coming into your account to their own email account and continue their attack on those who are emailing you directly.
- Create a spoof email account that looks very similar to your actual email address but with a different domain name. For example, if your email address is johnsomeguy@comcast.net, hackers may create a spoof email address like johnsomeguy@outlook.com. They can then use the spoof email address to impersonate you and scam your contacts in various ways.
- Attempt to hijack and take over other various online accounts, as the hackers can now receive/redirect security and login authentication emails.
- Delete all contacts in your address book, storage folders in your email account, or incoming email messages. This can cause you to lose important data and communication.
- Send spam or malicious emails from your email account to other people. This can damage your reputation and expose others to potential harm.
How You Can Protect Yourself From This Threat
If you suspect that your Comcast.net email account has been hijacked by hackers, you should take immediate action to secure it and prevent further damage. Here are some steps that you can take:- Change your password as soon as possible. Make sure that you use a strong password that does not use any common words or phrases. You can use a password manager or generator tool to help you create and remember a strong password.
- Check your email settings and rules. Look for any suspicious redirection or auto-forwarding rules that hackers may have set up and delete them. Also, check if hackers have changed any other settings, such as your signature, reply-to address, or recovery options.
- Scan your computer and devices for malware. Use reputable antivirus or anti-malware software to scan your computer and devices for any malware that hackers may have installed on them. Malware can compromise your security and allow hackers to access your email account or other accounts.
- Contact your contacts and inform them of the situation. Let them know that your email account has been hijacked and warn them not to open any emails or click on any links or attachments that they may have received from you recently. Also, ask them to report any suspicious emails that they may receive from the spoof email address that hackers may have created.
- Consider switching to a more secure email provider. Comcast.net email does not always offer some of the advanced security features that other email providers do, such as two-factor authentication (2FA). 2FA is when you need to enter a code or use another device to verify your identity when you log in to your email account. This adds an extra layer of protection against hackers who may have stolen your password. You may want to switch to an email provider that offers 2FA or other security features.
I hope this blog article has helped you understand how hackers can hijack your Comcast.net email account, what they can do with it, and how you can protect yourself from this threat. If you have any questions or comments, please feel free to leave them below.
Thursday, June 8, 2023
Gigabyte Motherboard BIOS Restore/Repair
Gigabyte Motherboard BIOS Restore/Repair
If your Gigabyte Motherboard BIOS becomes corrupt or damaged, and the board has a "Dual BIOS", you can use one of the methods below to restore/switch from your damaged/corrupted BIOS over to the other/working BIOS.
Method 1:
- Shut off your computer
- Hold the power button until your computer starts and shuts down again
- Press the power button again, your backup BIOS might now be loaded and the system may POST.
Method 2:
- Shut off your computer
- Hold power AND the reset button for about 10 sec, then release.
- If this method works, your system will now boot into the backup BIOS now.
Method 3:
Only use this method if nothing else has worked!!! You could potentially permanently damage your motherboard when attempting this last method!- Make sure you have a speaker built into your motherboard, or you have one attached to your motherboard's front panel connection header.
- You can short out pins 1 and 6 on the main BIOS chip by attaching a jumper to both pins (Pin #1 of the chip should be marked with a dot).
- As you short the pins, press the power button while you are still holding the jumper on the pins. You might want to have a friend help with this process so you don't accidentally short any other pins on the BIOS chip.
- Remove the jumper you're holding between pins 1 and 6 when you hear the POST beep.
- The backup BIOS should now be loaded and the system should POST.
Once you get the system up and running again, re-flash the other BIOS so you have yet another, alternative working BIOS.
Thursday, May 4, 2023
Microsoft Word/Microsoft Office: Turn off Entire Word Automatic Selection
How To Turn off Automatic Word Selection In Microsoft Office; Microsoft Word, Outlook, etc.
- Open Word, Excel, etc.
- Go to File, Options, then Advanced.
- Look for the option, "When selecting, automatically select the entire word" (it is enabled by default).
- You disable the 'feature' by deselecting its checkbox.
- Now Office will not automatically select the entire word when trying to select specific text!
Wednesday, April 19, 2023
How to Create a Local Account When Setting up a NEW Windows 11 Computer
How to Create a Local Account When Setting up a NEW Windows 11 Computer
We figured out a way to create a local account on Windows 11 when you are installing a fresh OS or setting up a new system! With this trick, you can steer clear of the Microsoft account requirement for Windows 11!
The easiest way to set up Windows without a Microsoft account is using a "dummy account" that was set up for this exact purpose. You don’t need to open Command Prompt, run commands, or disable the internet connection here. It’s a tried-and-tested method, and it just works without any fuss.
Here’s how to go about it:
- First, connect to the Wi-Fi and proceed with the Windows setup as normal. If you have a wired Ethernet connection, keep it connected.
- When you reach the Microsoft sign-in screen, enter a@a.com under the email field and click on “Next”. Do not worry, it’s a locked dummy account used for bypassing the Microsoft account requirement.
- On the next page, enter any password you like just to complete the steps.
- Now, click on “Sign in“.
- Since it’s a locked account, Microsoft will straight away start setting up a local account for you. You will see an “Oops, something went wrong” error, and then you can create a local account on Windows 11. Simply click on “Next”.
- Now you can now use Windows 11 without logging into a Microsoft account!
*UPDATE* 4-24-2024
The method listed above has been proving more and more ineffective in bypassing the mandatory requirement to set up a new Windows 11 computer, with a Microsoft account. But there's a simple trick for setting up a local account that involves issuing a command to keep Windows from requiring the Internet to install/set up and then cutting off the Internet at just the right time in the setup process. This works the same way whether you are doing a clean install of Windows 11 or following the OOBE process on a store-bought computer.
1. Follow the Windows 11 install process/setup process until you get to the "choose a country" screen:
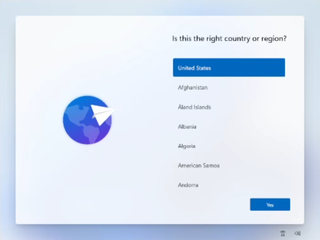
(Image credit: Tom's Hardware)
*Now's the time to cut off the Internet. However, before you do, you need to issue a command that prevents Windows 11 from forcing you to have an Internet connection.
2. Hit Shift + F10. A command prompt appears.
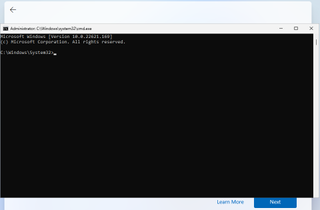
3. Type OOBE\BYPASSNRO to disable the Internet connection requirement.
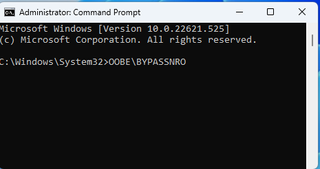
*The computer will reboot and return you to this screen.
4. Hit Shift + F10 again and this time Type ipconfig /release. Then hit Enter to disable the Internet. Alternatively you could also simply unplug the network cable if that's at all possible.
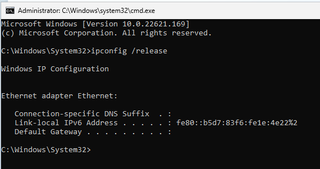
5. Close the command prompt.
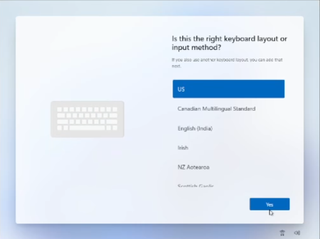
6. Continue with the installation, choosing the region. keyboard and second keyboard option.
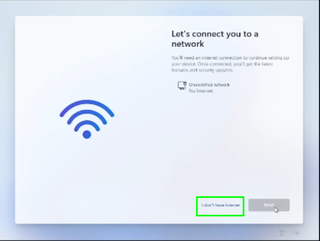
*A screen saying "Let's connect you to a network" appears, warning you that you need the Internet.
7. Click "I don't have Internet" to continue.
8. Click Continue with limited setup.
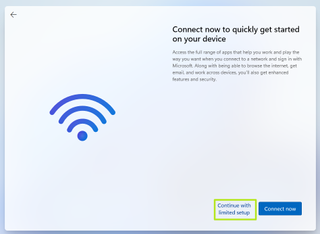
(Image credit: Tom's Hardware)
A new login screen appears asking "Who's going to use this device?"
9. Enter a username you want to use for your local account and click Next.
You are now setting up a local user account to be used, instead of being associated with a Microsoft Account!
Wednesday, April 12, 2023
Create a Content Marketing Strategy for Your Business
Create a Content Marketing Strategy for Your Business
What is Content Marketing?
Content marketing is the process of creating and distributing valuable, relevant, and consistent content to attract and retain a clearly defined audience and ultimately drive profitable customer action. Content marketing can include blog posts, ebooks, videos, podcasts, infographics, webinars, case studies, newsletters, social media posts, and more. The goal is to provide useful information to your audience that helps them solve their problems or achieve their goals.Why Do You Need a Content Marketing Strategy?
A content marketing strategy is a plan that outlines your goals, your audience, your content topics, your content formats, your content channels, your content calendar, and your content metrics. A content marketing strategy helps you:- Define your purpose and value proposition.
- Why are you creating content and what value do you offer to your audience?
- Identify and understand your target audience.
- Who are they, what are their needs and challenges, and what are their preferences and behaviors?
- Create relevant and engaging content.
- What topics will you cover, what formats will you use, and what tone and style will you adopt?
- Distribute and promote your content.
- Where will you publish and share your content, and how will you reach and attract your audience?
- Measure and optimize your content.
- How will you track and analyze your content performance, what metrics will you use, and how will you improve your results?
How to Create a Content Marketing Strategy in 5 Steps
Creating a content marketing strategy may seem daunting, but it doesn’t have to be. Here are five simple steps to follow:1) Set Your Goals
The first step is to define what you want to achieve with your content marketing. Your goals should be specific, measurable, achievable, relevant, and time-bound (SMART). For example:- Increase website traffic by 50% in six months
- Generate 100 new leads per month from ebooks
- Boost email open rate by 10% in three months
- Grow social media followers by 20% in one year
2) Know Your Audience
3) Choose Your Content Topics
The third step is to decide what topics you will cover in your content. You need to choose topics that are relevant to your audience’s needs and interests, as well as to your business goals and value proposition. You can use tools such as keyword research, competitor analysis, social media listening, surveys, and analytics to find out what topics are popular, trending, or in demand among your audience.4) Choose Your Content Format(s)
The fourth step is to determine what formats you will use for your content. You need to choose formats that suit your topics, your goals, and your audience’s preferences. You can use tools such as Google Analytics, social media insights, email reports, and feedback forms to find out what formats perform best for your content. Some of the most common formats are:- Blog posts: These are articles that provide information, tips, advice, opinions, or stories on a specific topic. They can help you drive traffic, generate leads, build authority, and educate your audience.
- Ebooks: These are long-form documents that offer in-depth knowledge, guidance, or solutions on a specific topic. They can help you generate leads, nurture prospects, showcase expertise, and establish trust.
- Videos: These are visual and audio recordings that demonstrate, explain, entertain, or inspire on a specific topic. They can help you increase engagement, boost awareness, build loyalty, and influence decisions.
- Podcasts: These are audio recordings that discuss, interview, teach, or share a specific topic. They can help you reach new audiences, create relationships, grow followers, and enhance credibility.
- Infographics: These are graphical representations that summarize, visualize, or compare data or information on a specific topic.
Social Media Marketing: How To Get Started (Work In Progress)
Marketing/Social Media Marketing 101 (BASICS)
The goal of consistent social media postings is for potential customers to be able to find your content and thusly find the product/service that you are providing. Experimenting with hashtags, keywords, posting in social media groups, and a sub-Reddit, helps people find you when looking up related topics and interests!Also, people like to see the behind-the-scenes of how stuff is made, produced, designed, and tested. Social media can give your customers (current and potential) a glimpse into what you're doing, how you make your product, and how your provided service is helping a customer. Social media can allow you to show people a more intimate and transparent look into what you do. That simple appreciation could turn into future business! If they see how dedicated you are, or they like your process and are impressed with how you do what you do, that all can generate business!
Plus it gives content for clients to be able to share with their friends! They see a post about something you've done, it reminds them of what you did for them, and they share that post with their friends/community!
FIRST THINGS FIRST: Have The Basics Covered
- Have professional artwork and/or logos made, along with a professional headshot if needed.
- Have a GOOD website. In this day in age, if your product doesn't have a good website, it can be the first impression a customer gets for your company. So you don't want "Just a website". Have a well-done website made for your product/service/company.
- Have a good first-page landing page
- Make sure to have an easy-to-find/get to About Us, Contact Form & Social Media links
- Have marketing material, business cards, a .Dot business card, etc ready to go.
- Try and have a few online payment methods set up so you can get paid no matter what:
- Venmo
- PayPal
- CashApp
- Square
- Stripe
Figure Out Your Target Audience
But don't just think about the general public! Also, think about businesses that may be interested as well. Coffee shops, wineries, government entities, corporate/commercial clients, etc.
You obviously want to try to sell to the general public, but maybe consider businesses-to-business opportunities, consider local/state/federal government agencies, big corporations, etc.
HAVE GOOD Contact Info on ALL SITES/PLATFORMS
- Web Site Address
- Phone Number(s)
- Email Addresses
- Messaging Services like Telegram, WhatsApp, etc.
- A Linktr.ee Address
- This is VERY handy! You can list ALL of your website links under one, easy to remember Linktr.ee address!
Social Media for Pictures and Information
By using Instagram you can actually also share your post directly to Facebook, Tumblr, and Twitter at the same time! The Instagram app allows you to share posts to multiple platforms!
Social Media for Video
- Tiktok
- Snapchat
- Youtube
- Twitch
Research Trends
- Etsy
Hashtags and Keywords
Search hashtags and certain keywords or interests/topics to see what hashtags and keywords are over-saturated, or topics that have little to no interactions. It is always worth a try to tag a post with a keyword with 17 million viewers, but your post will likely get lost in the sea of posts.So try to find hashtags, keywords, groups, etc that have a good amount of followers but if you use a hashtag with 1 Billion followers, it could get "lost at sea".
Also by experimenting with different hashtags and keywords, etc you will also narrow down what works and what does not work.
When you find keywords, hashtags, etc that work for you, THEN you can use that information to start doing paid advertising
Ideas On What To Post (Video, Text, or Picture):
- ALWAYS USE RESEARCHED HASHTAGS; ON ANY/ALL POSTS!
- Current world events
- Trending pop culture topics
- Behind the scenes of your product, service, etc.
- Highlight a product or service that you provide
- Your product or service in action!
- Giving back to the community? Post about it!
- Give free tips, give tutorials and how-to's, make product or service recommendations, etc. Anything that might be helpful but also related to your industry
- Highlight other local businesses that you like/use; maybe even cross-promote!
- Are you having a sale, running a special, or have an event coming up? Post about it!
Advertising/Paid Advertising
Once you have played around with keywords, hashtags, interests groups, etc you can take ALL of the information you have gained from your social media response on your posts, you can use that information to start doing targeted advertising.Posting Tips:
- Don't expect one single post to hit a home run! I usually use the psychology rule that if you see something 3 times (and even better, seeing something 3 times on 3 different platforms) will help people to be more likely to remember your post. But if they see the same thing on different platforms, it can give it more legitimacy and importance.
- I always recommend posting specific hashtags for 3-4 weeks at a time to see what the ACTUAL response to your posts is from those hashtags.
- When you post, try to post quality pictures! Don't go overboard with filters and edits, provide good contact information in ALL of your posts, make sure to use good grammar and punctuation, etc.
- The Instagram mobile app can post to Facebook, Instagram, Twitter, and Tumblr. You don't need to use all of those services, but at least get used to using posting to Instagram and Facebook, using the Instagram mobile app.
- Facebook groups, Reddit subreddits, etc can be good communities to interact with the community and be able to passively advertise yourself. Don't just join a group and start blasting what you do/sell! Interact with posts and if asked, or if it's brought up, or the timing seems right, refer nonchalantly to your business!







